US Government: Stop Dickering And Prepare For Post-Quantum Encryption Now
Us government stop dickering and prepare for post quantum reality us government stop dickering and prepare for post quantum cryptography us government stop dickering and prepare for colonoscopy us government stop dickering and prepare and enrich us government stop dickering and preparedness us government stop dickering and prepare with glenn us government stop dickering trazodonesuc us government stop dickering canviagrdfa us government stop dickering dtupharmyjn heuer us government stopwatch us government jobs usgovernment org
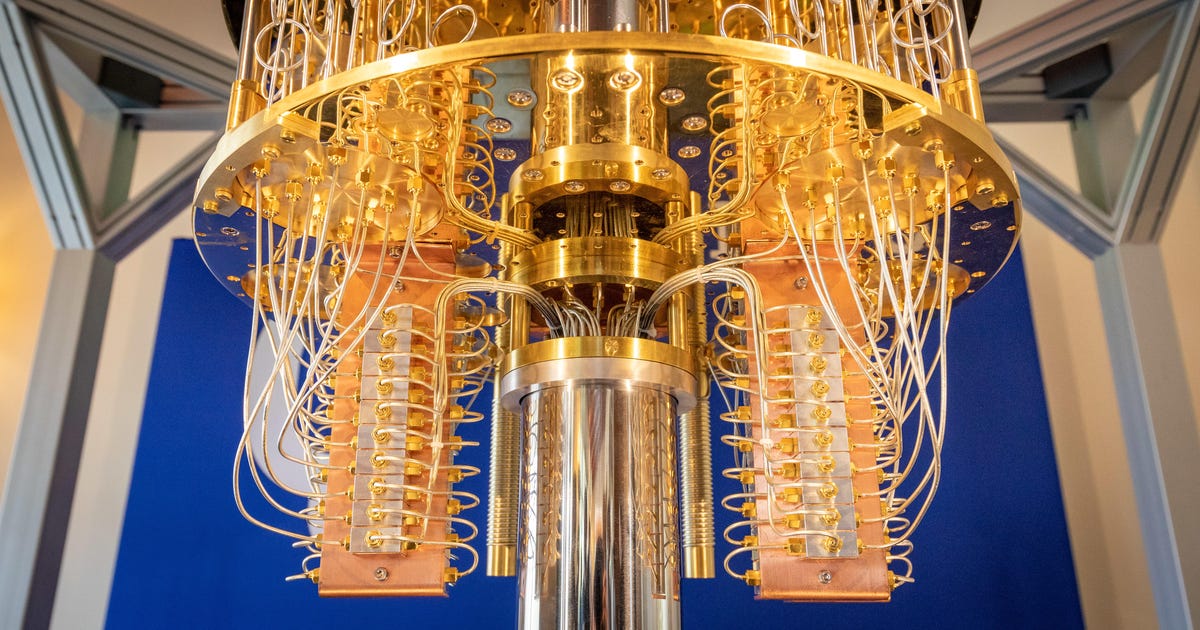
US Government: Stop Dickering and Prepare for Post-Quantum Encryption Now
If you're wondering when your company should start taking seriously the security problems that quantum computers pose, the answer is now, the US government says.
"Do not wait until the quantum computers are in use by our adversaries to act," the Cybersecurity and Infrastructure Security Agency said in a guide published Wednesday. "Early preparations will ensure a smooth migration to the post-quantum cryptography standard once it is available."
Quantum computers, which take advantage of the weird physics of the ultrasmall to perform calculations, are a nascent technology today. Companies like IBM, Intel, Google and Microsoft have joined a host of startups in investing billions of dollars in their development, though. And as they become more powerful, quantum computers could crack conventional encryption, laying bare sensitive communications.
That's why the US government's National Institute of Standards and Technology embarked on a search for post-quantum cryptography technology that would protect sensitive information even from quantum computers. With submissions and analysis from experts around the world, NIST picked four post-quantum encryption algorithms and is working to standardize them by 2024.
Quantum computers also could undermine cryptocurrencies, which also use today's cryptography technology.
Source
